Nessus
In computer security, Nessus is a proprietary comprehensive vulnerability scanning software. It is free of charge for personal use in a non-enterprise environment. Its goal is to detect potential vulnerabilities on the tested systems. For example:
Vulnerabilities that allow a remote cracker to control or access sensitive data on a system.
Misconfiguration (e.g. open mail relay, missing patches, etc).
Default passwords, a few common passwords, and blank/absent passwords on some system accounts. Nessus can also call Hydra (an external tool) to launch a dictionary attack.
Denials of service against the TCP/IP stack by using mangled packets
On UNIX (including Mac OS X), it consists of nessusd, the Nessus daemon, which does the scanning, and nessus, the client, which controls scans and presents the vulnerability results to the user. For Windows, Nessus 3 installs as an executable and has a self-contained scanning, reporting and management system.
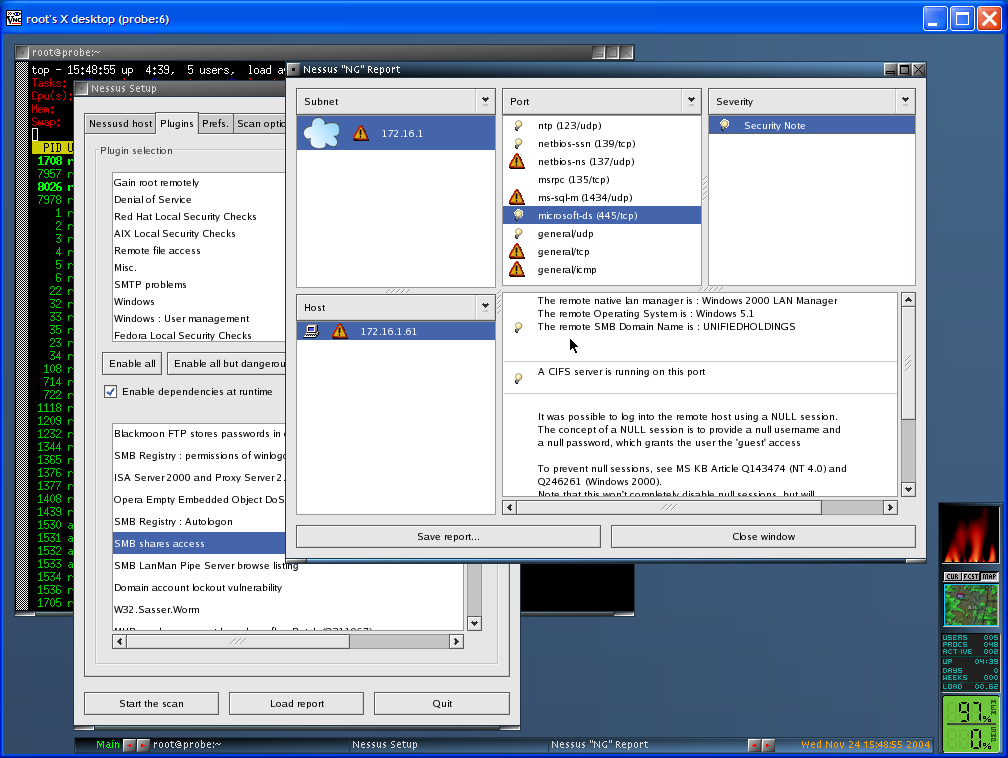
Nessus is the world's most popular vulnerability scanner, estimated to be used by over 75,000 organizations worldwide. It took first place in the 2000, 2003, and 2006 security tools survey from SecTools.Org
links